A topic I seem to repeatedly discuss at present: what does modern identity look like on macOS?
More broadly, what does cloud managed identity look like on all endpoints for now and future?
Important context: At time of writing, macOS 26 has just been released, however, none of the new Platform Single Sign-On (PSSO) features are supported by Okta or Entra ID.
- What’s new for enterprise in macOS Tahoe 26 – Apple Support
- Platform Single Sign-on for macOS – Apple Support (CA)
The goal of this post is to share opinionated principles of modern cloud driven identity on macOS and similar platforms, with examples of implementation detail that will change/evolve/mature/evolve over time.
I also acknowledge that Apple have changed their language from Mobile Device Management (MDM/MDM Server) to device management service to group platforms that use a mixture of old and new management protocols. I will use MDM interchangeably with device management service regardless if MDM (old) or DDM (Declarative Device Management aka new) protocols are involved.
Edit: credit to @trbridge, @hcodfrie, and @BigMacAdmin on Mac Admins Slack for pointing out some errors above.
Where Identity Is Used
User Identity on macOS has 4 touch points to influence outcomes in this discussion:
- Enrolment during Setup Assistant
- MDM assignment for policy
- macOS User account provisioning (login window)
- macOS User Account SSO and password sync
Enrolment & Policy
Enrolment & policy are generally related to one another and driven by the MDM (though some MDM vendors can change the assigned identity on the fly even if initially set to something else at enrolment).
Account Provisioning
Enrolment can influence or control account provisioning as part of Apple’s device management protocols to set or force the user account (nuances per MDM tool implementation).
SSO & Password Sync
A one to one device should NOT password sync IMO. Treat local password on Mac like an iPhone passcode or Windows Hello PIN. A token dance with MFA/passkeys/etc for Single Sign-On (SSO) access to resources beyond the Mac is the security gate, not the Mac login window.
Device Personas

I strongly believe that with cloud identities driving modern management practices, your device identities should come in 2 “persona” based flavours:
- One to one
- Shared
One to one is seen as a personalised device used by a single staff member over a short or long period of time. It typically holds 1 primary user session/data volume and needs to be reset to be used by someone else.
Shared is seen as a device that can be used by multiple people through a given day or week, such as a room based computer, like a computer lab. It supports multiple user sessions/data volumes that people can rapidly log in and out of.
Through the lens of the 4 touch points, here is what I recommend for each persona:
One to one:

- Authenticate at enrolment for the primary benefit of MDM policy based user assignment and optionally for Account Provisioning
- Enrolment has assigned your user for user assigned configs like wifi certs
- Enrolment can optionally prefill the local Mac user account short name with the prefix of the UPN or the user can create an account themselves. They set a local “passcode”.
- SSO for on premise resources uses the Kerberos SSO extension, XCreds, Jamf Connect, or similar. For cloud resources use the SSO extension with Company Portal or Okta Fastpass. No password sync. Only use PSSO if you need the benefits of a joined user assigned device object, possibility of Kerberos SSO and additional conditional access policy controls.
Shared Devices:
- Depending on your security posture and threat models, don’t authenticate at enrolment, or authenticate in a tech driven workflow. Local admin account creation may be automated or need to be created in setup assistant.
- User assignment is not required, but dynamic update is optional with capable MDM tooling
- Use XCreds or Jamf Connect for cloud driven identity user provisioning/login. Don’t require MFA.
- Use Kerberos SSO extension, XCreds, or Jamf Connect for password sync (cloud sync if available) and Kerberos Tickets. Use SSO extension with Company Portal or Okta Fastpass for cloud resource SSO.
Do not use PSSO TODAY for shared devices as the per user registration is buggy and a bad user experience IMO.
If the changes for PSSO in macOS 26 and associated implementation changes by IDPs turn out as expected, my recommendation likely changes.
From AD to Entra with Windows Hello
With or without PSSO, the guidance above works. It follows a similar line of thinking to WHfB (Windows Hello for Business) which already makes sense if you’re an Entra shop.
These concepts may be harder to swallow if you’re still very much an AD (Active Directory) shop.
If your organisation’s answer to autopilot device deployment for Windows was hybrid join instead of Entra join, you know who you are 😅
The one login to rule them all paradigm people were used to with AD joined devices makes sense for shared devices. It doesn’t make sense for personalised devices in 2025 IMO.
It has the “always on network” assumption.
It also assumes resource access control is pretty flat and not dynamic at all.
WHfB Components
WHfB promotes the concept of:
- Local Credential = PIN
- Biometric = Face/Finger
- Directory credential = dir user password
- Directory trust/SSO = PRT granting
Let’s compare these to Apple device concepts:
iPhone/iPad (one to one):
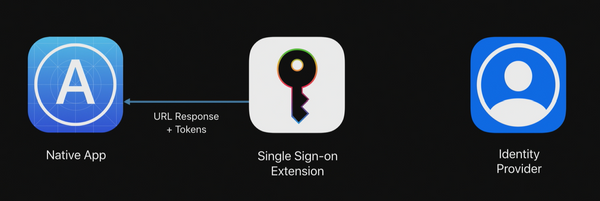
- Passcode
- Face/Touch ID
- Sign in to Outlook/SaaS apps
- MS Authenticator w SSO extension inc MFA dance
Mac (one to one):
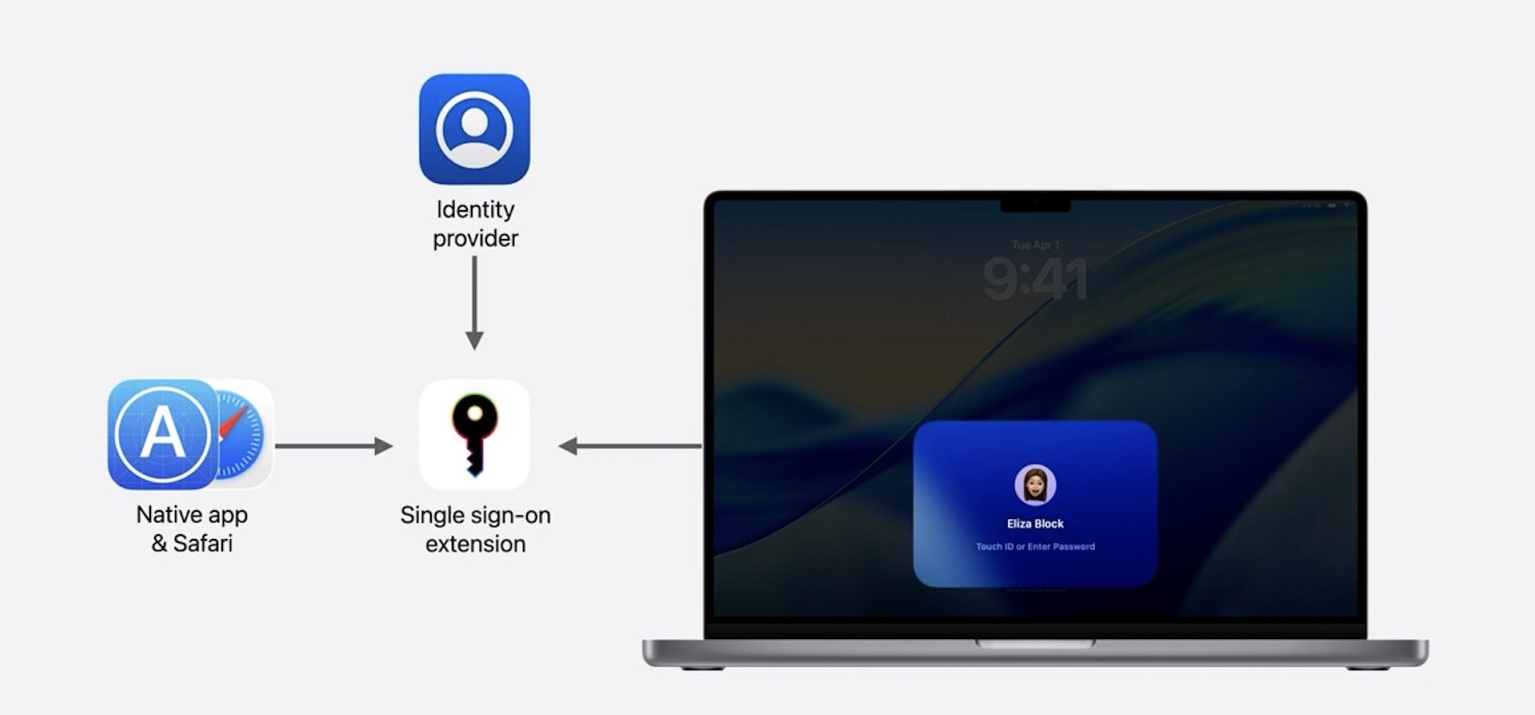
- Local User Password
- Touch ID
- Sign in to Outlook/SaaS apps
- Company Portal w SSO extension inc MFA dance
Shared Windows Devices
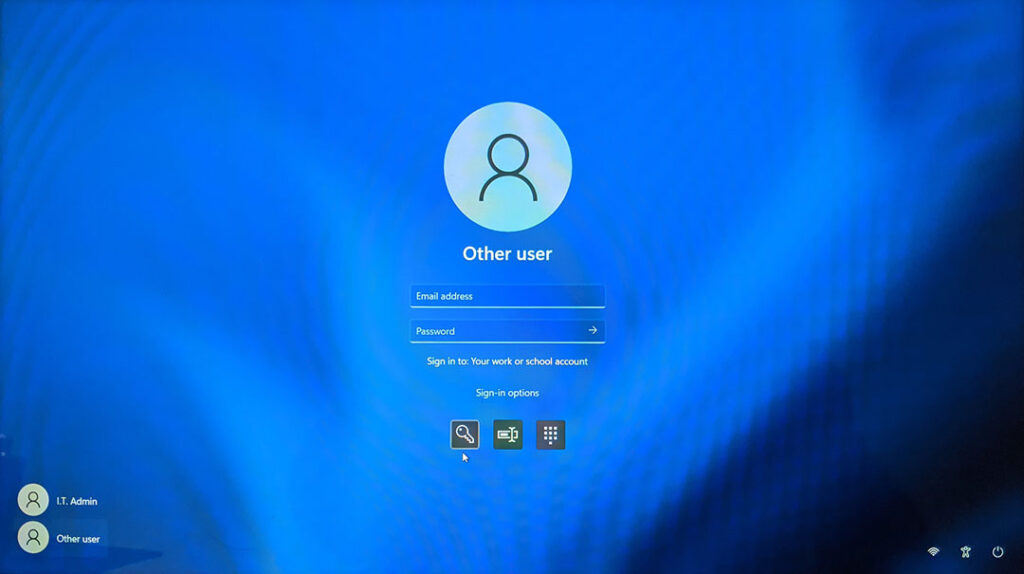
For shared devices, the model of Windows Entra Joined is:
- Directory credential at login window (future state passwordless, using something you have like a passkey)
- The FIRST sign in to a cloud app/Entra auth resource gets you to MFA dance to get your PRT and then SSO is your friend from there.
When To Enforce MFA
I see a lot of confusion around MFAs place when cloud identity is involved with macOS, Windows and other endpoints.
In the AD Bound device paradigm, you always logged in with the current (or cached) credential of your networked user account. Unless you had a fancy implementation from RSA, you probably didn’t worry about hardware tokens or other forms of multi factor authentication at the computer login screen.
That single login WAS your single sign on to all organisation resources connected to the Kerberos motorway, starting with the TGT (Ticket Granting Ticket) that gave you subsequent tickets for each file, print, or authenticated web server you tried to access.
In a cloud identity driven world, it’s your cloud authentication POST LOGIN WINDOW that grants your primary refresh token (PRT). That authentication flow is subject to conditional access policies, and the subsequent access tokens it generates are also subject to their own conditional policies.
That’s Not A Token! This Is A Token!
There is a widespread misconception that WHfB is how you enable or disable your MFA requirement for a cloud resource SSO experience with Windows login.
If you have conditional access policy that says you must MFA to get a PRT and/or access certain cloud resources (like OneDrive), it’s doesn’t matter if you’re logging in from a Entra Joined/managed device or not at all basic level.
What matters is that you perform MFA in USER SPACE to get a PRT and start granting access tokens.
WHfB makes MFA the first thing you do AFTER the windows login screen on an Entra Joined device. In order to get this benefit they REQUIRE you to set a PIN and/or Biometric authentication method.
Without it, you can sign into the PC with just a password, but you don’t have access to any cloud resources until that FIRST MFA to get a full PRT prompted by the first app sign in.
They both don’t require MFA to sign into, especially for a shared device, and only get you to confirm user presence and factors of trust when you’re accessing resources BEYOND the computer.
If you exclude the device/user/source IP from MFA the login window can SSO to apps like OneDrive, similar to the on prem AD sign in days if it suits your security/threat models.
Truthfully? Not a great idea 😅
Back To The Mac
Gee, that was a lot of Windows talk on a Mac blog: yes, yes it was.
The reality is we operate in a lot of technology environments set by standards derived from roots in Kerberos and LDAP, packaged into the Active rather than Open flavour of directory.
Microsoft embraced a while ago that the future was not the old ways, but identity founded on a different set of rules. You couldn’t confine to the network perimeter, but had to design identity systems that had infinite collaborators at a global scale.
This new set of rules says how we authenticate and prove our identity will need to become increasingly complex in its defence to threats, which meant the focus of protection needed to change.
We’re trying to prevent a threat actor from accessing unauthorised resources, not block a user from logging into their machine and recover from a legitimate problem.
If you authenticate and prove levels of trust to provision a computer and your user account, why do you need to prove that trust every time you hit the login window and every time your PRT needs to refresh?
Keep access to the device easy (just a password or local pin or biometric) and the sign in to your cloud resources via the PRT access tokens policed by your conditional access policy, managing the threats to your organisation’s most valued assets (your “Crown Jewels”).
- Enrol/provision a Mac using known credential – with MFA
- Login to a Mac with your local PIN/biometric (1:1) or known credential (shared) – no MFA
- Get access to your PRT for SSO and re-auth with conditions are not met – with MFA
I hope this posts helps you and your organisation move forward with cloud managed identity for the modern endpoint.
Further References
- Windows Hello for Business overview | Microsoft Learn
- XCreds – Twocanoes Software
- Jamf Connect – Jamf Connect Documentation | Jamf
- Kerberos Single Sign-on extension with Apple devices – Apple Support (AU)
- Configure an SSO extension on managed macOS devices | Okta Identity Engine
- Configure Desktop Password Sync for macOS 14 | Okta Identity Engine
- Microsoft Enterprise SSO plug-in for Apple devices – Microsoft identity platform | Microsoft Learn
- macOS Platform Single Sign-on (PSSO) overview – Microsoft Entra ID | Microsoft Learn
- Enable Kerberos SSO to on-premises Active Directory and Microsoft Entra ID Kerberos Resources in Platform SSO – Microsoft Entra ID | Microsoft Learn